v2.27.7 Armory Continuous Deployment Release (Spinnaker™ v1.27.3)
2023/02/16 Release Notes
Note: If you’re experiencing production issues after upgrading Spinnaker, rollback to a previous working version and please report issues to http://go.armory.io/support.
Required Armory Operator version
To install, upgrade, or configure Armory 2.27.7, use Armory Operator 1.70 or later.
Security
Armory scans the codebase as we develop and release software. Contact your Armory account representative for information about CVE scans for this release.
Breaking changes
Kubernetes version for deployment targets
Armory CD 2.26 no longer supports Kubernetes deployment targets prior to version 1.16.
Impact
Any Kubernetes deployment target must run version 1.16 or higher. If you try to deploy to clusters older than 1.16, you may see errors like the following in the UI:
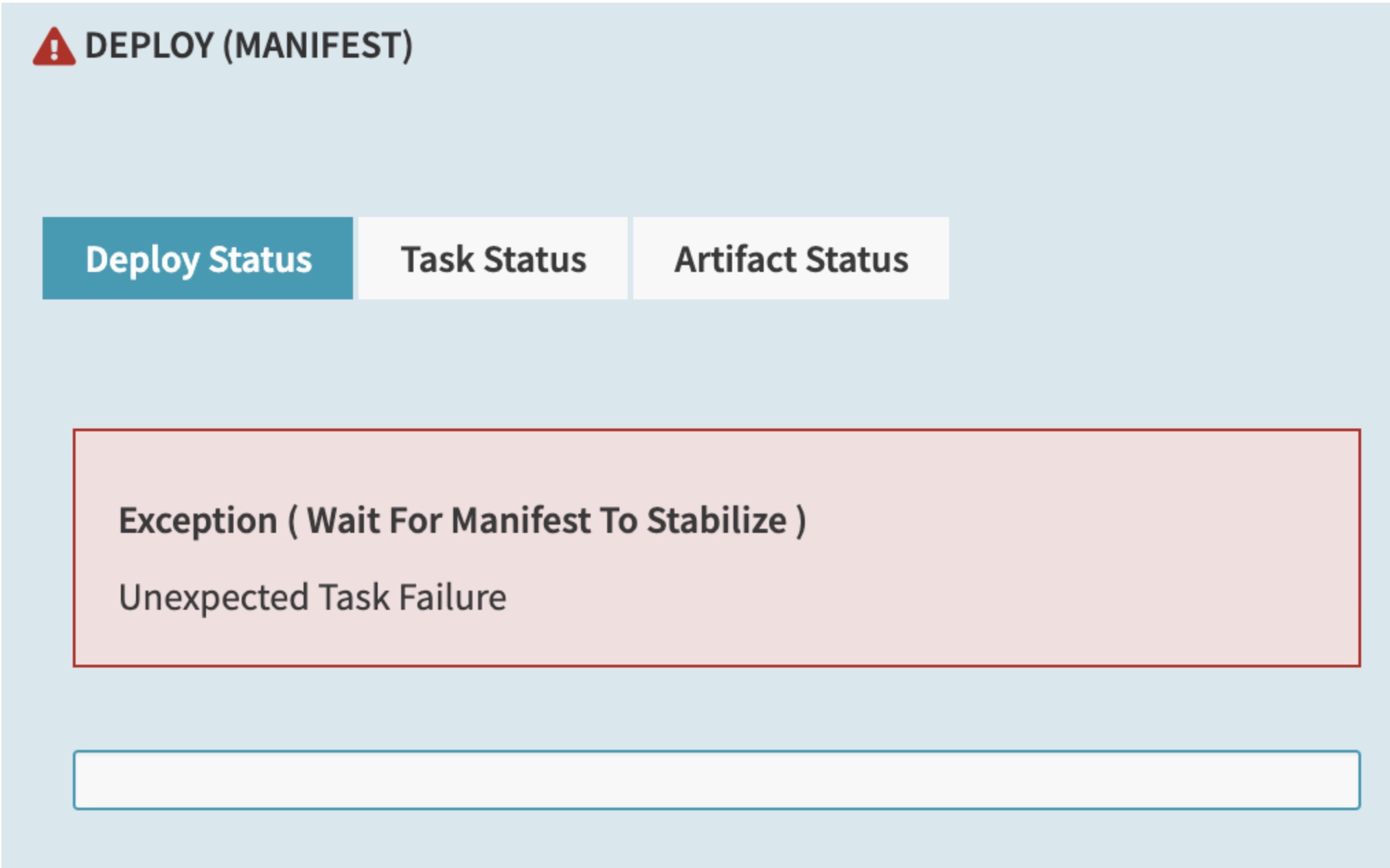
Additionally, errors like the following appear in the Clouddriver logs:
2021-05-04 21:17:16.032 WARN 1 --- [0.0-7002-exec-9] c.n.s.c.k.c.ManifestController : Failed to read manifest
com.netflix.spinnaker.clouddriver.kubernetes.op.handler.UnsupportedVersionException: No replicaSet is supported at api version extensions/v1beta1
at com.netflix.spinnaker.clouddriver.kubernetes.op.handler.KubernetesReplicaSetHandler.status(KubernetesReplicaSetHandler.java:98) ~[clouddriver-kubernetes.jar:na]
2021-05-05 14:29:09.653 WARN 1 --- [utionAction-538] c.n.s.c.k.c.a.KubernetesCachingAgent : kubernetes/KubernetesCoreCachingAgent[1/1]: Failure adding relationships for service
com.netflix.spinnaker.clouddriver.kubernetes.op.handler.UnsupportedVersionException: No replicaSet is supported at api version extensions/v1beta1
at com.netflix.spinnaker.clouddriver.kubernetes.op.handler.KubernetesReplicaSetHandler.getPodTemplateLabels(KubernetesReplicaSetHandler.java:167)
Workaround
If you are affected by this change, perform the following tasks to update your applications:
- Upgrade the Kubernetes clusters that you are trying to deploy to. They must run version 1.16 or higher.
- If you have manifest files using deprecated APIs, update them to use newer APIs. For more information on which APIs are deprecated in each Kubernetes version and how to migrate, see the Kubernetes Deprecated API Migration Guide.
Introduced in: Armory CD 2.26.0
Kubernetes infrastructure in the UI
Starting in 2.26, the UI has been updated to more closely follow immutable infrastructure principles.
When you navigate to the Infrastructure tab in the UI for an application that has the Kubernetes provider configured, actions that change the Kubernetes infrastructure (such as Create or Delete), including Clusters, Load Balancers, and Firewalls, are no longer available.
Impact
Users do not see these actions in the UI by default. You must configure the UI to display them if you want your users to be able to perform them through the UI.
Workaround
Whether or not these actions are available in the UI is controlled by the following property in settings-local.yml:
window.spinnakerSettings.kubernetesAdHocInfraWritesEnabled = <boolean>;
This setting does not completely prevent users from modifying Kubernetes infrastructure through Armory CD. To do so, you must use the Policy Engine and write policies using the spinnaker.http.authz package.
If you use the Policy Engine to control which user roles can see the UI actions and be able to use them, you must set this property to true. Setting the value to false hides the buttons for all users regardless of whether you grant specific users access to the buttons through the Policy Engine.
This property affects Kubernetes infrastructure only. The behavior is slightly different depending on if the application has only the Kubernetes provider configured or Kubernetes and other providers, such as AWS.
If the application only has the Kubernetes provider configured, the following applies:
- When set to
true, this property causes the UI to function as it did in previous releases. This allows people to manually create and delete Kubernetes infrastructure from the UI. - When set to
false, this property causes the actions to be unavailable to users. This prevents users from manually creating and deleting Kubernetes infrastructure from the UI. The users can still view the infrastructure but cannot make changes through the UI.
If the application includes Kubernetes and other providers, the following applies:
- When set to
true, this property causes the UI to function as it did in previous releases. This allows people to manually create and delete Kubernetes infrastructure from the UI. Users can continue to select whether they want to create Kubernetes or other infrastructure in the UI. - When set to
false, this property causes Kubernetes to be unavailable as an option when trying to modify infrastructure from the UI. Users can still make changes to infrastructure for the application from cloud providers, such as AWS, but not Kubernetes.
Introduced in: Armory CD 2.26.0
Halyard deprecation
Halyard is no longer supported for installing Armory Continuous Deployment 2.27.0 and later. Use the Operator. For more information, see Halyard Deprecation.
Due to changes in the underlying services, older versions of some plugins may not work with Armory Continuous Deployment 2.27.x or later.
The following table lists the plugins and their required minimum version:
| Plugin | Version |
|---|---|
| Armory Agent for Kubernetes Clouddriver Plugin | 0.10.0 |
| App Name | 0.2.0 |
| AWS Lambda | 1.0.9 |
| Evaluate Artifacts | 0.1.1 |
| External Accounts | 0.2.0 |
| Observability Plugin | 1.3.1 |
| Policy Engine | 0.2.1-rc |
Breaking changes are kept in this list for 3 minor versions from when the change is introduced. For example, a breaking change introduced in 2.21.0 appears in the list up to and including the 2.24.x releases. It would not appear on 2.25.x release notes.
Known issues
SpEL expressions and artifact binding
There is an issue where it appears that SpEL expressions are not being evaluated properly in artifact declarations (such as container images) for events such as the Deploy Manifest stage. What is actually happening is that an artifact binding is overriding the image value.
Workaround:
2.27.x or later: Disable artifact binding by adding the following parameter to the stage JSON: enableArtifactBinding: false.
2.26.x or later: Change the artifact binding behavior in spec.spinnakerConfig.profiles.clouddriver (Operator) or clouddriver-local.yml (Halyard) to the following, which causes artifacts to only bind the version when the tag is missing:
kubernetes:
artifact-binding:
docker-image: match-name-only
This setting only binds the version when the tag is missing, such as image: nginx without a version number.
Affected versions: 2.26.x and later
Pipelines-as-Code GitHub comments
There is a known issue where Pipelines-as-Code can generate hundreds of comments in a GitHub Pull Request (PR) when updates are made, such as when a module that is used by multiple dinghyfiles gets changed. These comments may prevent the GitHub UI from loading or related API calls may lead to rate limiting.
Affected versions: 2.26.x and later
Workaround:
You can either manually resolve the comments so that you can merge any PRs or turn the notifications that Pipelines-as-Code sends to GitHub.
For information about about how to disable this functionality, see GitHub Notifications.
Secrets do not work with Spring Cloud Config
If you enable Spring Cloud Config all the properties (e.g. Docker) using Secrets are not resolved when Spring Cloud tries to refresh.
Affected versions:
- 2.26.x and later
Known Affected providers in Clouddriver:
- Kubernetes
- Cloudfoundry
- Docker
Workaround:
Do not use secrets for properties that are annotated with @RefreshScope.
Pipelines-as-Code GitHub comments
There is a known issue where Pipelines-as-Code can generate hundreds of comments in a GitHub Pull Request (PR) when updates are made, such as when a module that is used by multiple dinghyfiles gets changed. These comments may prevent the GitHub UI from loading or related API calls may lead to rate limiting.
Affected versions: Armory CD 2.26.x and later
Workaround:
You can either manually resolve the comments so that you can merge any PRs or turn the notifications that Pipelines-as-Code sends to GitHub.
For information about about how to disable this functionality, see GitHub Notifications.
Early Access features
Dynamic Rollback Timeout
To make the dynamic timeout available, you need to enable the feature flag in Orca and Deck.
On the Orca side, the feature flag overrides the default value rollback timeout - 5min - with a UI input from the user.
{
"yaml,"
"orca.yml,"
"rollback:"
"timeout:"
"enabled: true"
}
On the Deck side, the feature flag enhances the Rollback Cluster stage UI with timeout input.
window.spinnakerSettings.feature.dynamicRollbackTimeout = true;
The default is used if there is no value set in the UI.
Pipelines-as-Code multi-branch enhancement
Now you can configure Pipelines-as-Code to pull Dinghy files from multiple branches in the same repo. Cut out the tedious task of managing multiple repos; have a single repo for Spinnaker application pipelines. See Multiple branches for how to enable and configure this feature.
Automatically Cancel Jenkins Jobs
You now have the ability to cancel triggered Jenkins jobs when a Spinnaker pipeline is canceled, giving you more control over your full Jenkins workflow. Learn more about Jenkins + Spinnaker in this documentation.
Fixed
- Updated google cloud SDK to support GKE >1.26
Spinnaker Community Contributions
There have also been numerous enhancements, fixes, and features across all of Spinnaker’s other services. See the Spinnaker v1.27.3 changelog for details.
Detailed updates
Bill Of Materials (BOM)
Here’s the BOM for this version.
Expand
artifactSources:
dockerRegistry: docker.io/armory
dependencies:
redis:
commit: null
version: 2:2.8.4-2
services:
clouddriver:
commit: dc29b777268954cce13b1b36b152d4e2a493caa9
version: 2.27.7
deck:
commit: be6776c69c18743de1df214acaa500250569a146
version: 2.27.7
dinghy:
commit: ca161395d61ae5e93d1f9ecfbb503b68c2b54bc5
version: 2.27.7
echo:
commit: 3204f90e951562245c62430d863617c34b3a0826
version: 2.27.7
fiat:
commit: b3ca6748d2377454949420613e7912748ea00b52
version: 2.27.7
front50:
commit: 5e1fe36c4b8df29cc9cb4d7af581a44b0ca44e59
version: 2.27.7
gate:
commit: adf9732bc7b3c8df48b21b86ef9783efcadec78b
version: 2.27.7
igor:
commit: 9e2d7946da19c803eb0bd12e888c5119528a364c
version: 2.27.7
kayenta:
commit: 5a1efcefddfe78f37550f5bee723570e3737ce04
version: 2.27.7
monitoring-daemon:
commit: null
version: 2.26.0
monitoring-third-party:
commit: null
version: 2.26.0
orca:
commit: b239fa305820b1102d38fe4d0beeaca847c0f4f2
version: 2.27.7
rosco:
commit: f4164fdcfa275b62e0c0fefbe26b5cbd845c543d
version: 2.27.7
terraformer:
commit: f845ba2fc760c46b98794a10c32cc2b713c7c9e0
version: 2.27.7
timestamp: "2023-02-08 07:01:33"
version: 2.27.7
Armory
Armory Orca - 2.27.6…2.27.7
- chore(cd): update base orca version to 2023.02.03.15.10.20.release-1.27.x (#585)
Armory Rosco - 2.27.6…2.27.7
Armory Deck - 2.27.6…2.27.7
- chore(cd): update base deck version to 2023.0.0-20230203161357.release-1.27.x (#1295)
Armory Echo - 2.27.6…2.27.7
Armory Clouddriver - 2.27.6…2.27.7
- chore(cd): update base service version to clouddriver:2023.01.27.17.41.53.release-1.27.x (#784)
Armory Fiat - 2.27.6…2.27.7
Armory Front50 - 2.27.6…2.27.7
Dinghy™ - 2.27.6…2.27.7
Armory Gate - 2.27.6…2.27.7
Armory Igor - 2.27.6…2.27.7
Armory Kayenta - 2.27.6…2.27.7
Terraformer™ - 2.27.6…2.27.7
Spinnaker
Spinnaker Orca - 1.27.3
- fix(timeout): Added feature flag for rollback timeout ui input. (backport #4383) (#4384)
Spinnaker Rosco - 1.27.3
Spinnaker Deck - 1.27.3
- fix(timeout): Added feature flag for rollback timeout ui input. (backport #9937) (#9939)
Spinnaker Echo - 1.27.3
Spinnaker Clouddriver - 1.27.3
- feat(gke): Enables gcloud auth plugin for 1.26+ GKE clusters (backport #5847) (#5852)
Spinnaker Fiat - 1.27.3
Spinnaker Front50 - 1.27.3
Spinnaker Gate - 1.27.3
Spinnaker Igor - 1.27.3
Spinnaker Kayenta - 1.27.3
Feedback
Was this page helpful?
Thank you for letting us know!
Sorry to hear that. Please tell us how we can improve.
Last modified December 6, 2023: (a0529dfe)